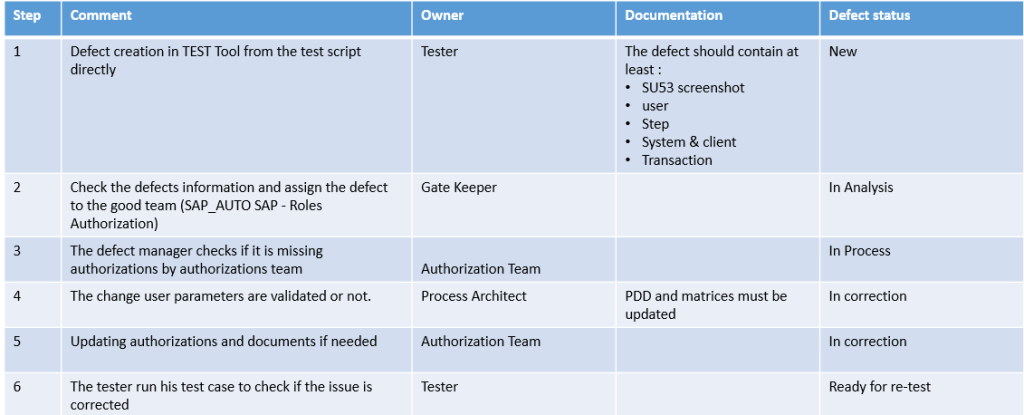
SAP Fiori Application
SAP Users Type
| Types of user in SAP | Uses and Purpose |
| Dialog Users | Named user who login to the user and have to logon in the system with his/her id and password. |
| Service Users | Service user is also can login to the system and password not expired and many user can login at a time. Mainly used for testing purpose. |
| System Users | Used for system to schedule jobs and background process |
| Communication Users | Used to connect other system and RFC call |
| Reference Users | To provide indirect access to the Dialog users |
Project and Developer roles
Developer roles
Developer role needs access to design the UI Application and ABAP program and enhancement
Basis Role/Security Admin
Basis and Security role used by administrator to manager the system and access to the user and design the end user roles
Function team
Functional team have access for the designing the organization structure and functional design
Core Team
Key business users created in development system to check the configuration and executing business tcodes and Fiori applications
Production Users
End Users
All the Business users created in the Production system
Support Team
Basis, Security, Developer and Functional consultant also created in Production system for business support with no change access of any configuration data or master data.
SAP OSS id
This id created in production system and password will be shared with SAP in case of SAP support on any application
System user/Communication Users
System id created in production system to support system activities and connecting GRC system with Fiori system
Role Matrix
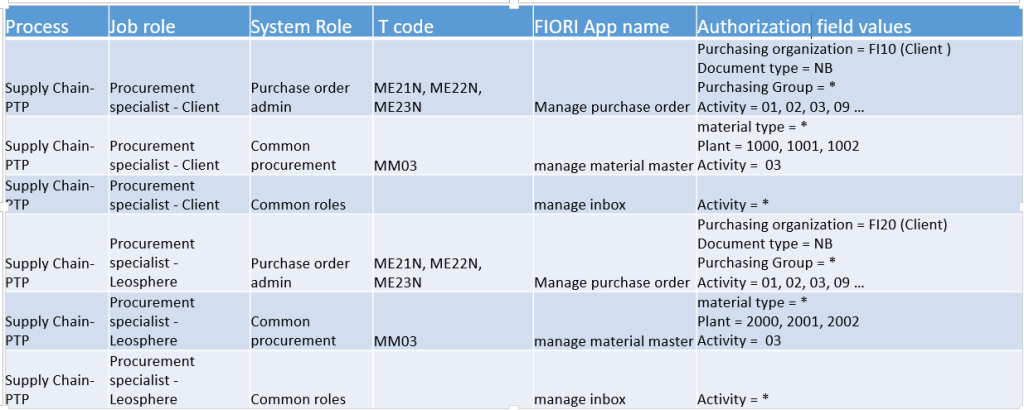
Types of Roles in SAP
- Single roles
Provide the access to the user using a normal single roles
- Master Derived roles
This role provide used to have some business function for different organization data.
All the derived role can provide the same application to users restricted with Area of responsibility
Eg Sales manager Finland, Sales Manager US
- Composite roles
This role is combined the single and derived roles and used for better maintenance and support
Business Role Design Process
The Security team will work closely with the Business and Technical teams to define, develop, test, and implement end-user access. The application security approach will be developed for the following end user types
- DEV, QA and Production business users
- DEV, QA and Production security and basis technical support
A security role will be made up of the following key elements
- Fiori Application/Transaction codes to be included in a role based on tasks defined in Business Function Matrix.
- Fiori Catalog and Group added into the role menu based on tasks defined in Business Function Matrix.
- Organizational level restrictions (e.g. certain Company Codes) for the Master role
- Respective derived roles based on above restrictions
- Tables to be viewed or maintained by the role
- Other functional restrictions or user exits within transactions (e.g. specific document Types) • Field Level restrictions will need to be in place to restrict the user’s ability to see specific data on screen. The restrictions are provided in business functions matrix.
End User Role design Process and example
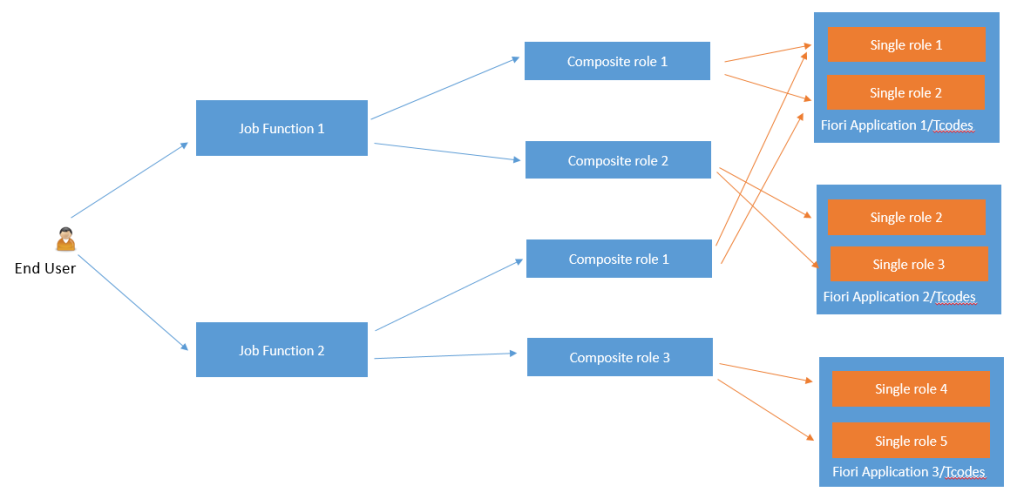
Defect Correction Process – Testing Phase